FIPS 140-2 Non-Proprietary Security Policy, Version 0.8
March 17, 2016
Sonus SBC 7000 Session Border Controller
© 2016 Sonus Networks, Inc.
This document may be freely reproduced and distributed whole and intact including this copyright notice.
Page 28 of 32
3.4
Additional Usage Policies
This sections notes additional policies below that must be followed by module operators:
As noted above, operator access to the BMC is provided over two external ports: an RS-232 serial port
and a 1Gbps Ethernet port (called the BMC Field Service Port). The CO must use this port in order to
accomplish the module's initial setup and configuration as described in section 3.1.1 above. Beyond this,
the BMC's external ports shall not be used while the module is operational; use of the BMC's external
ports is prohibited while the module is operating in its FIPS-Approved mode. The CO shall ensure that
operators do not directly access the module via the BMC's external ports for any purpose.
EC Diffie-Hellman with encryption strength less than 112 bits and Triple-DES keying option 2 shall not be
used in the FIPS Approved mode of operation.
In case the module's power is lost and then restored, a new key for use with the AES GCM
encryption/decryption shall be established.
The module allows for the loading of new firmware, and employs an Approved message authentication
technique to test its intgrity. However, to maintain an Approved mode of operation, the CO must ensure
that only FIPS-validated firmware is loaded. Any operation of the module after loading non-validated
firmware constitutes a departure from this Security Policy.
3.5
Non-FIPS-Approved Mode
During operation, the module can switch modes on a service-by-service basis between an Approved mode of
operation and a nonApproved mode of operation. The module will transition to the nonApproved mode of
operation when the "Establish SSH Session" service is invoked using the curves P-192, K-163, or B-163. The
module transitions back to the Approved mode of operation upon the utilization of an Approved security
function.
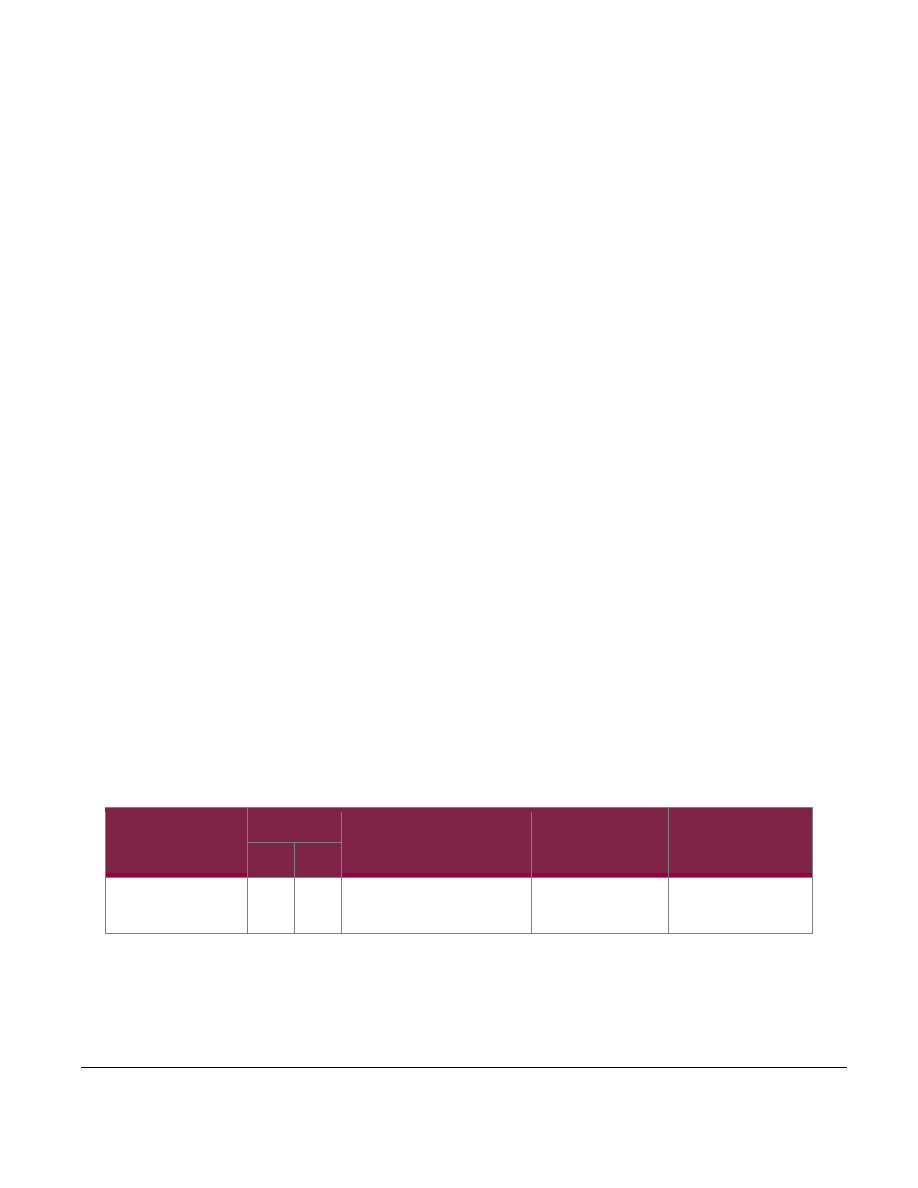
The module supports the Crypto Officer and User roles while in the non-Approved mode of operation. Table 9
below lists the service(s) available in the non-Approved mode of operation.
Table 9 Non-Approved Services
Service
Operator
Description
Input
Output
CO
User
Establish SSH Session
(non-compliant)
Establish remote session using
SSH protocol
Command
Command response/
Status output

