FIPS 140-2 Non-Proprietary Security Policy, Version 0.8
March 17, 2016
Sonus SBC 7000 Session Border Controller
©2016 Sonus Networks, Inc.
This document may be freely reproduced and distributed whole and intact including this copyright notice.
Page 13 of 32
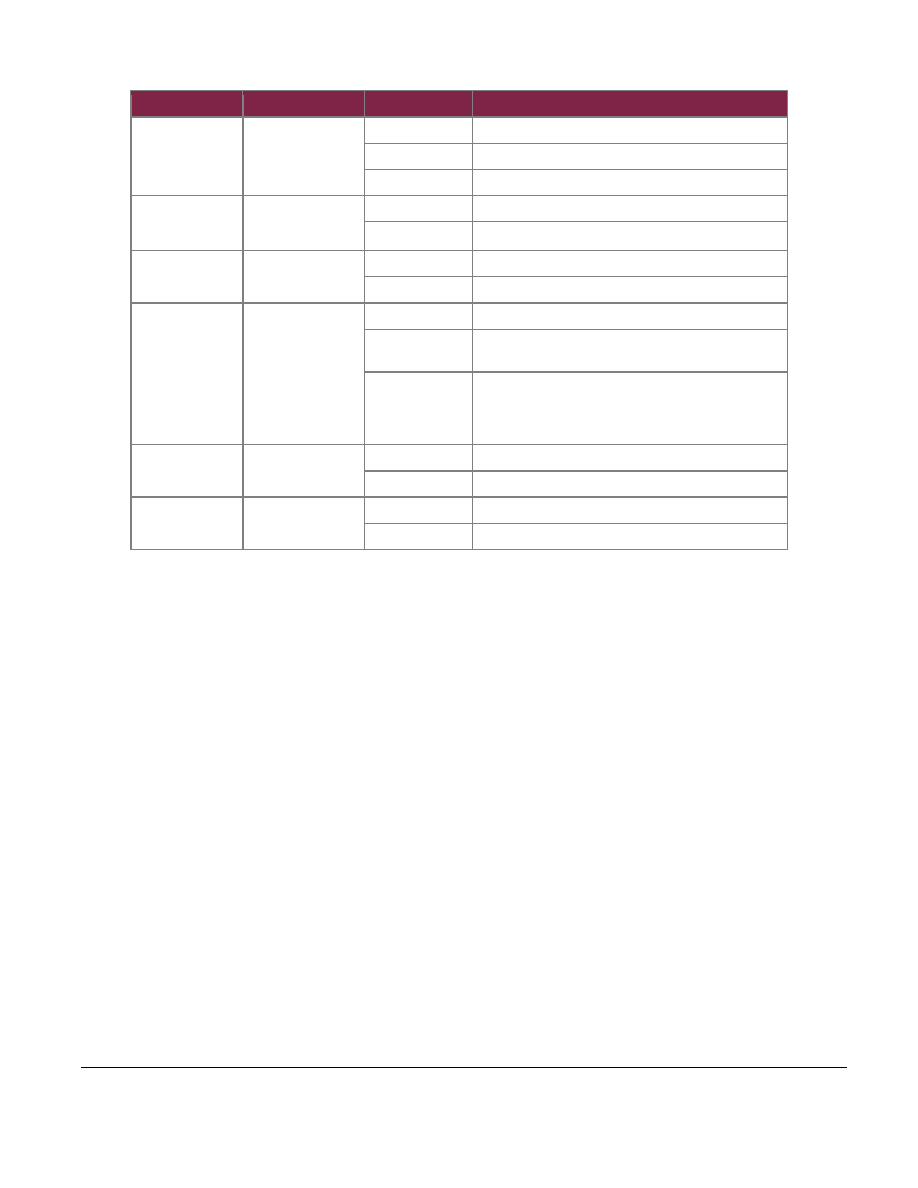
LED
Description
Color
Definition
FP Alarm LED
Indicator of module
Critical/Major
Failure
OFF
The module is in no alarm condition state.
AMBER
The module is in major alarm condition state.
RED
The module is in critical alarm state.
FP Locator LED
Indicator of module
Identifier
OFF
The module is not being identified.
ON or Blinking
The module is being user identified.
BP Locator LED
Indicator of module
Identifier
OFF
The swappable module is not being identified.
ON or Blinking
The swappable module is being user identified.
BP H/S LED
Indicator of
operations status of
the hotswappable
module when
chassis
management
software brings
down the module.
OFF
The hotswappable module is running normal.
SOLID BLUE
The hotswappable module is completely down and safe
for removal.
FLASHING BLUE
The hotswappable module is shutting down or going
offline.
Power Supply LED
Indicator of state of
the power supply
OFF
The power supply is not working.
GREEN
The power supply is operational.
Ethernet and SFP
Port LEDs
Indicator of link and
activity status
GREEN
A cable is connected and the link is up.
Blinking GREEN
Activity is present on the link.
Apart from these indicators, the alarms events are also logged into log file.
2.4
Roles and Services
The sections below describe the module's roles and services, and define any authentication methods employed.
2.4.1 Authorized Roles
As required by FIPS 140-2, the module supports two roles that operators may assume:
Crypto Officer The CO is responsible for initializing the module for first use, which includes the
configuration of passwords, public and private keys, and other CSPs. The CO is also responsible for the
management of all keys and CSPs, including their zeroization. Lastly, the CO is the only operator that can
configure the module into FIPS-Approved mode of operation. The CO also has access to all User services.
User The User has read-only privileges and can show the status and statistics of the module, show the
current status of the module, and connect to the module remotely using HTTPS and SSH.
2.4.2 Operator Services
Descriptions of the services available to the Crypto Officer role and User role are provided in the Table 5 below.
The keys and CSPs listed in Table 5 indicate the type of access required using the following notation:
R Read: The CSP is read.
W Write: The CSP is established, generated, modified, or zeroized.

