FIPS 140-2 Non-Proprietary Security Policy: IBM Security XGS 3100, XGS 4100, XGS 5100, and XGS 7100
Document Version 0.9
© IBM Security
Page 12 of 50
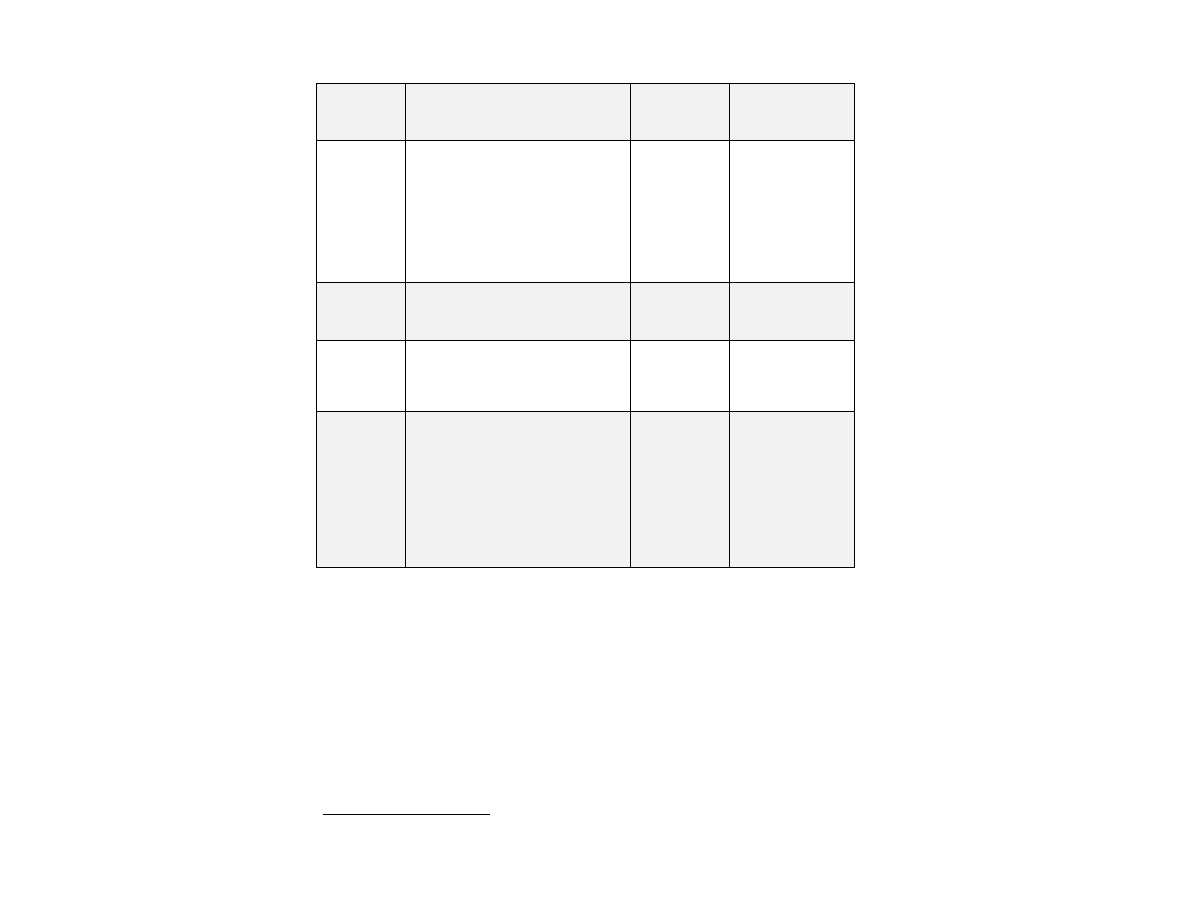
HMAC
HMAC-SHA-1, HMAC-SHA-224, HMAC-SHA-
256, HMAC-SHA-384, HMAC-SHA-512
XGS3100: 2077
XGS4100: 2079
XGS5100: 2080
XGS7100: 2081
Message verification
AES
AES-128-CMAC, AES-192-CMAC, AES-256-
CMAC. ECB, CBC, CFB1, CFB8, CFB128 & OFB
AES_CCM 128, 192,or 256 bit keys (SP800-
38C)
AES_GCM 128, 192,or 256 bit keys (FIPS 197,
SP800-38D)
AES_XTS 128, 256 bit keys (FIPS SP 800-38E)1
XGS3100: 3280
XGS4100: 3282
XGS5100: 3283
XGS7100: 3284
Data encryption /
decryption
Triple-DES
Triple-DES 192-bit keys in ECB, CBC, CFB64,
and OFB mode, CMAC
XGS3100: 1867
XGS4100: 1869
XGS5100: 1870
XGS7100: 1871
Data encryption /
decryption
DRBG 800-90A
HMAC_DRBG (SHA-1, SHA-224, SHA-256,
SHA-384, SHA-512), HASH_DRBG (SHA-1,
SHA-224, SHA-256, SHA-384, SHA-512),
CTR_DRBG (AES-128- ECB, AES- 192-ECB,
AES-256- ECB)
XGS3100: 738
XGS4100: 740
XGS5100: 741
XGS7100: 742
DRBG
DSA
[(1024, 160) bits; (2048, 224) bits; (2048,
256) bits; (3072, 256) bits]
(SHA-1, SHA-224, SHA-256, SHA-256)
XGS 3100
DSA: #937
XGS 4100
DSA: #939
XGS 5100
DSA: #940
XGS 7100
DSA: #941
Verify operations
Table 4 Algorithm Certificates (GSKIT)
The TLS, SSH, and SNMP protocols have not been reviewed or tested by the CAVP and CMVP. Please see
NIST document SP800-131A for guidance regarding the use of non FIPS-approved algorithms.
2.3.2 Non-Approved but Allowed Algorithms
The module implements the following non-FIPS approved but allowed algorithms:
·
True Random Number Generator (TRNG), a non-deterministic RNG (NDRNG) used to seed the
DRBG.
·
GSKIT: RSA Key Wrapping Encrypt / Decrypt (2048, 3072 bits) Allowed to be used in FIPS mode
(key wrapping; key establishment methodology provides 112 or 128 bits of encryption strength)
1 AES XTS mode was CAVS validated but not implemented within the module.

