© Copyright 2004
Nortel Networks
Page 7 of 18
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
characters (A-Z, a-z, and 0-9) with repetition, the
chance of a random attempt falsely succeeding is
1 in 56800235584.
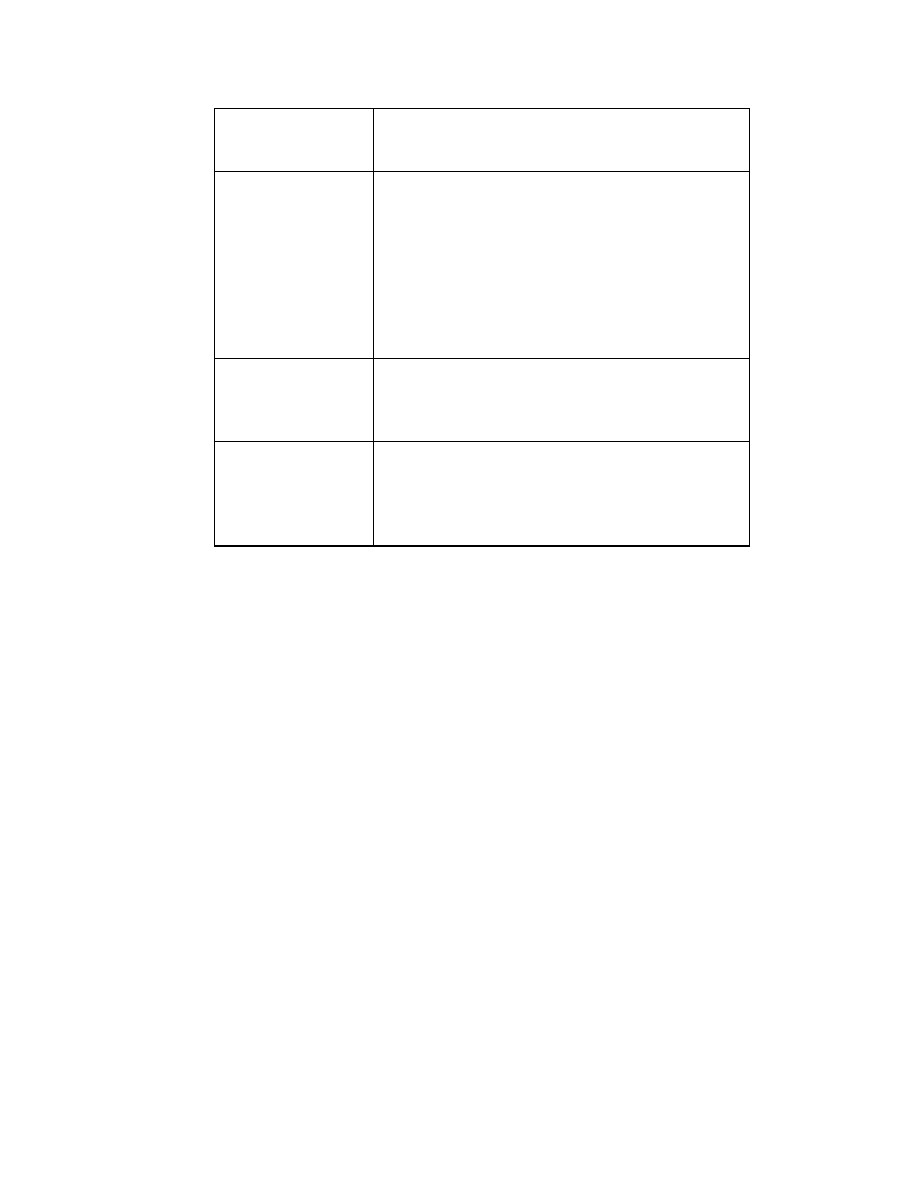
RADIUS shared
secret key
The RADIUS server authenticates to the module
using a hash of the shared secret key combined
with other information. The minimum size of this
shared secret key configured by the Crypto-
Officer must be 6 characters in length in FIPS
mode. Assuming usage of only the 94 ASCII
characters capable of being entered through a
keyboard with repetition, the chance of a random
attempt falsely succeeding is 1 in 689869781056.
Public Key based
The module supports authentication using RSA
public keys for IPSec and TLS. The probability
of a random attempt to falsely succeed is much
lesser than 1 in 2^512.
Pre-shared keys
This method of authentication derives the pre-
shared keys based on the user id and password
using SHA-1. The probability of a random
attempt to falsely succeed is much less than 1 in
2 ^ 160.
The module supports both an internal and external RADIUS server based authentication.
The Crypto-Officer can either configure the authentication to be performed using data in
an internal LDAP or RADIUS server, or using an external RADIUS or LDAP server. If
the RADIUS server is used, only a CHAP based authentication must be used. In other
words, PAP must be disabled.
Physical Security
The Contivity 1700, 2700 and 5000 are multi-chip standalone modules and meet all
physical security requirements for FIPS 140-2. The platforms provide production grade
equipment, industry-standard and a strong enclosure, and the systems meet Federal
Communication Commission (FCC) Electromagnetic Interference (EMI) compatibility
requirements. The document Configuring the Contivity in FIPS Mode defines the
required procedures to apply tamper-evidence labels across the module's cover so that the
Crypto-Officer can detect any attempt to open the box. It also details logging all access to
the box by logging each time the tamper evidence seals are broken with permission of the
Crypto-Officer. The module also has an audible alarm that activates when the front cover
is removed.
Cryptographic Key Management and Algorithms
Critical Security Parameters of the Module

