HID Global Digital ActivID Applet Suite v2.6.2B on Oberthur Technologies ID-One Cosmo v7
FIPS 140-2 Security Policy
© Copyright 2015 HID Global Corporation / ASSA ABLOY AB
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
9
PIN Verification Authentication Method
The external entity submits an identifier and corresponding PIN. The PIN is compared to the stored reference for
that identifier. The character space for PINs is enforced by the module to be in the alphanumeric range (62
possible values). The minimum PIN length of 6 characters is enforced by the module. The probability that a
random attempt will succeed using this authentication method is:
1/(62^6) = 1.8E-11
The module restricts authentication attempts to 15 tries, so the probability that a random attempt will succeed
over a one minute interval is:
15/(62^6) = 2.6E-10
6.0
Services
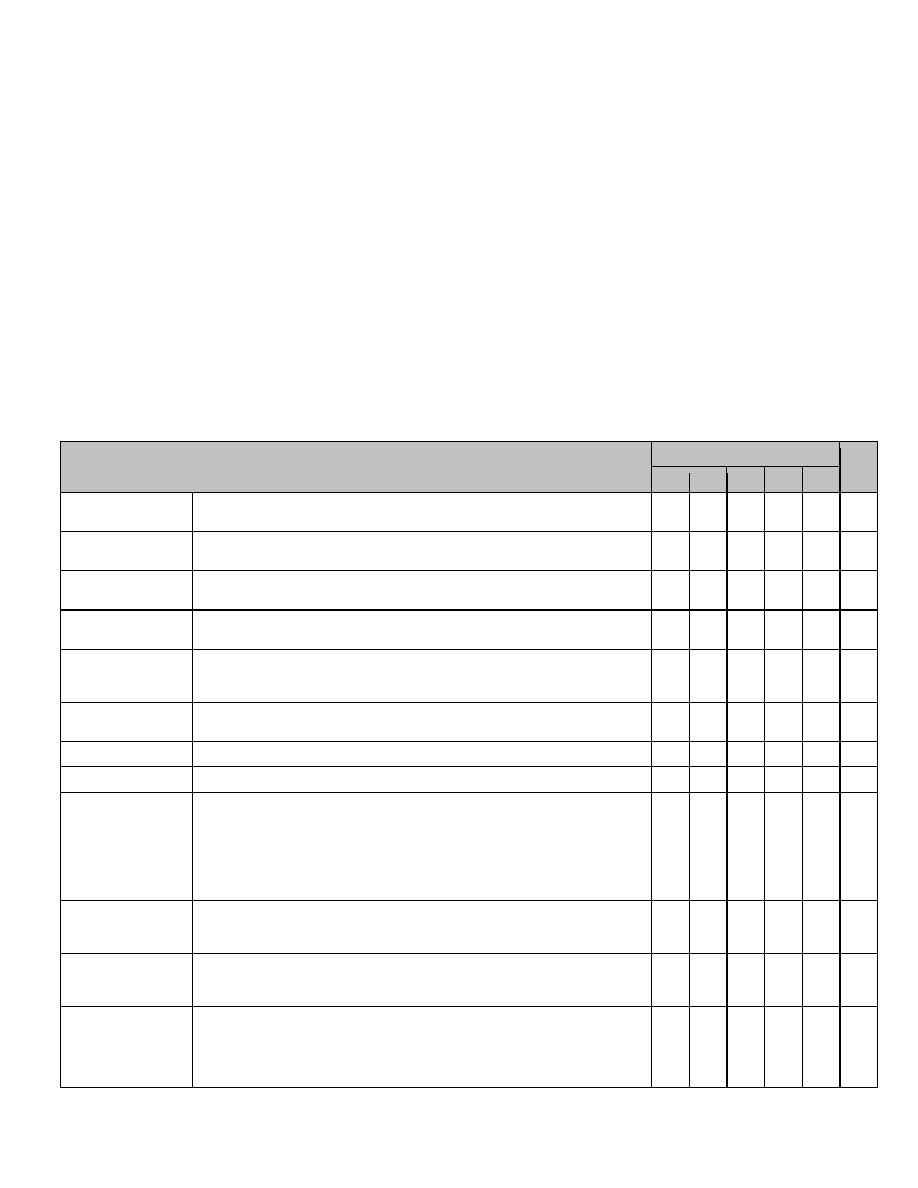
Table 8 list the services implemented by the module, separated into the services implemented by the platform and
by the ActivID Applet Suite, respectively. All services are available via the contact interface. Services available via
the contactless interface are marked in the CL column.
TABLE 9: Module Services by Role
Platform Services
Roles
CL
CA
AP
CH
AO
PO
Module Reset (power
cycle)
Powering on or resetting the module; reinitializes the module, including invoking all
power-on self-tests described in Section 7.0.
X
DELETE
This command is used by the CA to delete a uniquely identifiable object. The object
may be an Application, a load file, or a key set.
X
X
X
EXTERNAL
AUTHENTICATE
This command is used by the CA to open a Global Platform Secure Channel
Session with the Issuer Security Domain.
X
X
X
GET DATA
The GET DATA command is used to retrieve public data from the selected
application. No CSP can be read using this service.
X
X
X
X
X
X
GET STATUS
This command is used by the CA to retrieve identification and life cycle status
information for all applications, executable load files, and security domains present
in the module.
X
X
X
INITIALIZE UPDATE
This command is used by the CA to initiate a Global Platform Secure Channel
Session, setting the key set version and index.
X
X
X
INSTALL
This command is used by the CA to add an application to the module.
X
X
LOAD
This command is used by the CA to load patch or applet code.
X
X
PUT KEY
This command is used by the CA to add or replace Security Domain keys. Keys are
loaded protected by the double encryption of the global Platform Secure Channel
and a KCV is included in the transmission to ensure integrity of the key loading
operation.
This command is also used by the CA to load RSA public keys such as the Token
Verification Key or the DAP Verification Key. These keys are used for Delegated
Management and DAP verification as specified by Global Platform.
X
X
X
SELECT
This command is used for selecting an application on a specific logical channel. A
successful selection logs out the role currently active on the same logical channel,
if any. In the applet suite context SELECT can be used to select a Load File.
X
X
X
X
X
X
SET STATUS
This command is used to manage the lifecycle state of the card. The use of SET
STATUS with the TERMINATE qualifier provides the required Zeroization service,
along with removal and reinsertion of the card into the reader.
X
X
X
STORE DATA
This command is used by the CA to transfer data to the module. It is also used to
clear the audit log and to modify the contactless capabilities (activate/deactivate a
contactless stealth mode, or to allow only non-identifiable information to leak out of
the contactless interface until the terminal can be authenticated) to increase the
privacy protection of the user.
X
X
X

