Introduction
FortiGate-1000C/1240B/3140B/3240C FIPS 140-2 Security Policy
01-505-211830-20130705
3
http://docs.fortinet.com/ · Feedback
Introduction
The FortiGate product family spans the full range of network environments, from SOHO to
service provider, offering cost effective systems for any size of application. FortiGate
appliances detect and eliminate the most damaging, content-based threats from email and
Web traffic such as viruses, worms, intrusions, inappropriate Web content and more in
real time -- without degrading network performance. In addition to providing application
level firewall protection, FortiGate appliances deliver a full range of network-level services
-- VPN, intrusion prevention, web filtering, antivirus, antispam and traffic shaping -- in
dedicated, easily managed platforms.
All FortiGate appliances employ Fortinet's unique FortiASICTM content processing chip
and the powerful, secure, FortiOSTM firmware achieve breakthrough price/performance.
The unique, ASIC-based architecture analyzes content and behavior in real time, enabling
key applications to be deployed right at the network edge where they are most effective at
protecting enterprise networks. They can be easily configured to provide antivirus
protection, antispam protection and content filtering in conjunction with existing firewall,
VPN, and related devices, or as complete network protection systems. The modules
support High Availability (HA) in both Active-Active (AA) and Active-Passive (AP)
configurations.
FortiGate appliances support the IPSec industry standard for VPN, allowing VPNs to be
configured between a FortiGate appliance and any client or gateway/firewall that supports
IPSec VPN. FortiGate appliances also provide SSL VPN services using TLS 1.2 in the
FIPS-CC mode of operation.
Security Level Summary
The module meets the overall requirements for a FIPS 140-2 Level 2 validation.
.
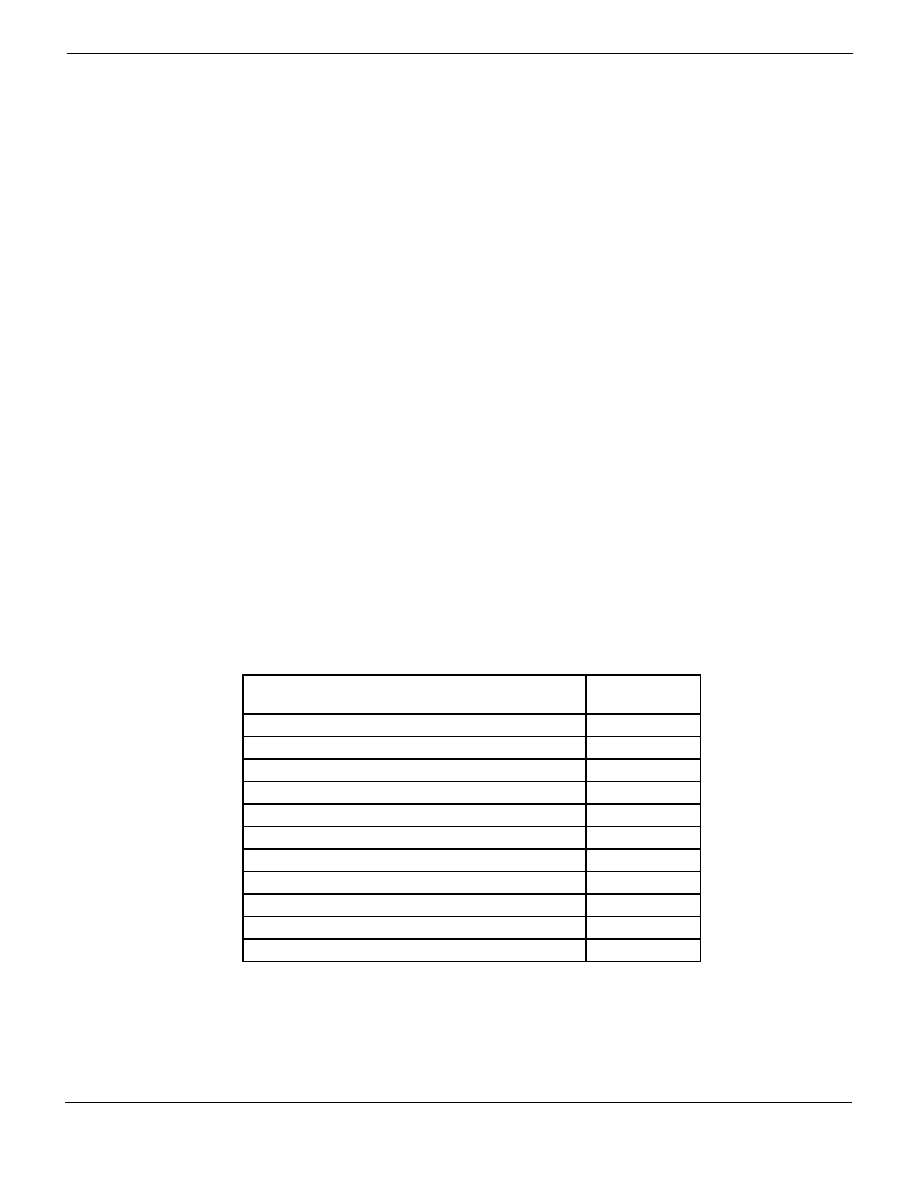
Table 1: Summary of FIPS security requirements and compliance levels
Security Requirement
Compliance
Level
Cryptographic Module Specification
2
Cryptographic Module Ports and Interfaces
3
Roles, Services and Authentication
3
Finite State Model
2
Physical Security
2
Operational Environment
N/A
Cryptographic Key Management
2
EMI/EMC
2
Self-Tests
2
Design Assurance
3
Mitigation of Other Attacks
2

