Non-Proprietary Security Policy, Version 1.0
March 19, 2012
Cisco Tandberg C40, C60, and C90 codecs
Page 12 of 26
© 2012 CISCO
This document may be freely reproduced and distributed whole and intact including this copyright notice.
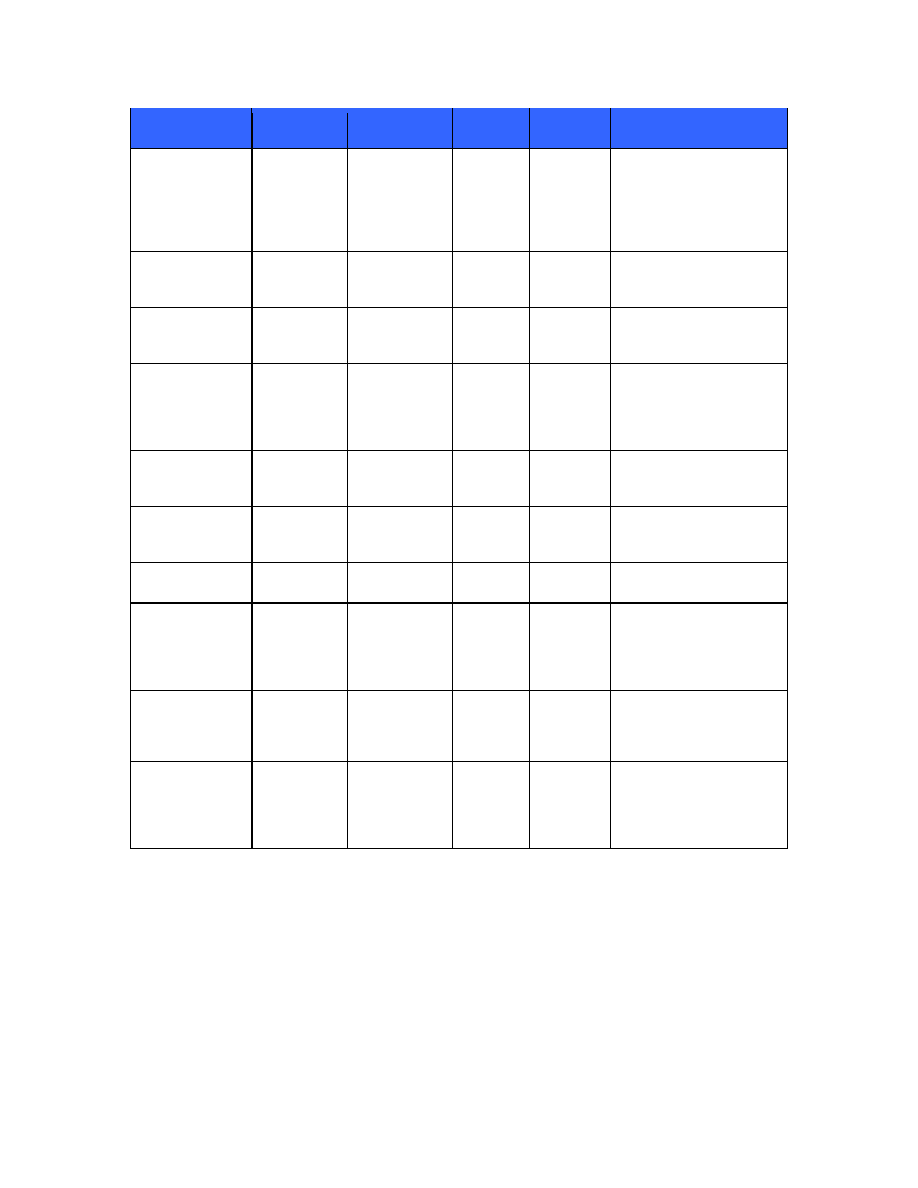
Key/
Key Component
Type
Generation
Storage
Zeroization
Use
sRTP salting key
Salting key
Generated
using the
module's
Approved
DRBG
Stored in
volatile
memory
When
session is
termintated
Used to generate the
Initialization vector of the
SRTP encryption stream
SIP TLS session
keys
HMAC-SHA1
AES128
Derived
according to the
TLS protocol
Stored in
volatile
memory
When
session is
terminated
Used for user
authentication/encryption
over TLS connection on SIP
SIP TLS certificate
private key
RSA/DSA
Provided by
Crypto Officer
Stored on
flash in
plaintext
On factory
reset
With SIP TLS client
certificate
HTTPS TLS
session key
HMAC-SHA1
Derived
according to the
TLS protocol
Stored in
volatile
memory
When
session is
terminated
Data
authentication/encryption
for TLS sessions (HTTPS
client, HTTPS server,
Syslog)
HTTPS TLS
certificate and
private key
RSA/DSA
Provided by
Crypto Officer
Stored on
flash in
plaintext
On factory
reset
With HTTPS TLS
handshake
HTTPS TLS
session encryption
key
Triple-DES
AES CBC 128
bit
Derived
according to the
TLS protocol
Stored in
volatile
memory
When
session is
terminated
Data encryption for TLS
sessions
RNG seed key
Seed key
Using non-
Approved RNG
Stored on
flash
On factory
reset
Used for RNG operations
Passwords
Operator
password
Generated each
time a user
changes his/her
password
Hashed
using SHA-
256 and
stored on
flash
On factory
reset
Password hashes for users
are stored on flash.
Passwords are not stored in
cleartext
File storage
cryptographic key
AES-128
Generated from
random data on
module
initialization
Stored on
NOR-Flash
On factory
reset
Used for encrypting the file
storage on NAN-Flash
Firmware Integrity
Key
DSA public
key
Exists within the
firmware binary
Stored on
flash
Public key
not
required to
be
zeroizable
Used for checking integrity
of the firmware on every
power-up
2.4.1
Key Generation
The module uses SP800-90 DRBG RNG to generate cryptographic keys. This RNG is FIPS-Approved as indicated
by FIPS PUB 140-2.
The seed for the SP800-90 DRBG RNG is provided by a non-Approved RNG, which collects entropy from the
Ethernet receiver.

