Non-Proprietary Security Policy, version 2.1
September 1, 2009
TrustedFlash v1.0 microSD
Page 9 of 29
© 2009 SanDisk Corporation
This document may be freely reproduced and distributed whole and intact including this copyright notice.
1.
Data Input
2.
Data Output
3.
Control Input
4.
Status Output
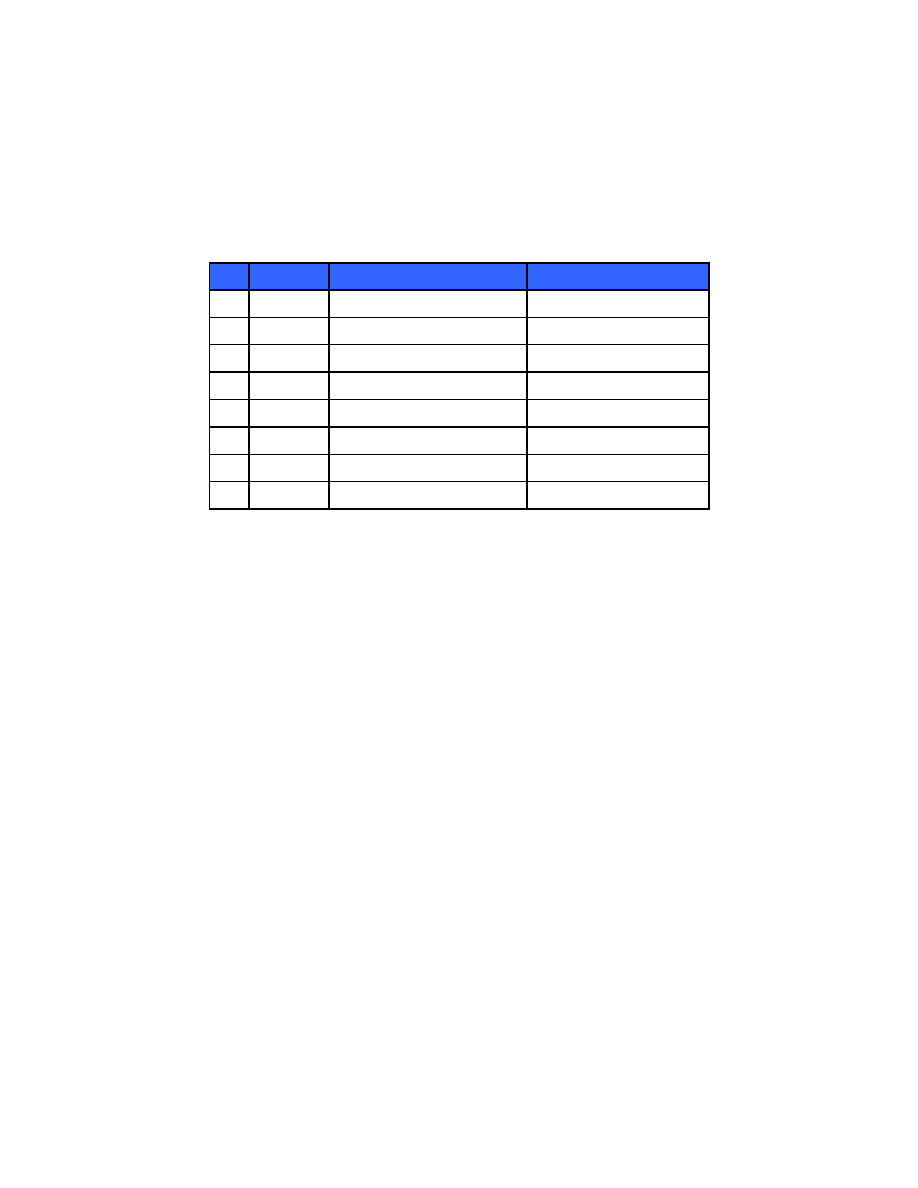
The rightmost columns of Table 2 map the physical interface of the module to the FIPS 140-2 interfaces.
Table 2 Physical and FIPS 140-2 Interface Mappings for SD Mode
Pin
Name
Bond Wire Pin Assignment
FIPS 140-2 Interface
1
DAT2
Data line [bit 2]
Data input, data output
2
CD/DAT3
Card detect/Data line [bit 3]
Data input, data output
3
CMD
Command response
Control input, status output
4
VDD
Supply voltage
Power
5
CLK
Clock
Control input
6
VSS
Supply voltage ground
Power
7
DAT0
Data line [bit 0]
Data input, data output
8
DAT1
Data line [bit 1]
Data input, data output
All data is passed to the cryptographic module using standard write and read commands to a buffer. Therefore, from
the host's point of view, sending a command means writing data to a special file on the memory device, which is
used as the buffer file. Getting information from the module is done via reading data from the buffer file.
2.3 Roles and Services
The module supports two roles: a Crypto-Officer role and a User role. A Crypto-Officer as an operator can log into
the system Access Control Records (ACRs) and/or root ACR Group (AGP) that can access all services. Any entity
attempting to use the TrustedFlash commands is required to login to the TrustedFlash system through an ACR. An
ACR can be considered a user account. Different ACRs may share common interests and privileges within the
system, such as secured domains from which to read and write data. ACRs with attributes in common are grouped in
ACR groups called AGPs. AGPs and the ACRs are organized in hierarchical trees. The AGP tree structure enables
the module to handle multiple applications. This is where each application comprises a collection of identifiable
entities represented as an ACR on the tree. Mutual exclusion between the applications is achieved by ensuring there
is no cross-talk or cross-communication between the tree branches.
A tree of the Approved mode is a tree with the root AGP configured with the authentication and key establishment
method defined as one of the FIPS-Approved schemes shown in Table 7. New ACRs created on a tree of the
Approved mode are also working in the Approved mode because the "Tree Authentication Restrictions" command
has been executed to the tree during the tree creation process. See Section 3 "Secure Operation" of this document for
more information.
Non-Approved mode trees are not supported when the module has been configured to operate in the Approved mode
of operation. After FIPS-Approved trees are created and configured according to security policy instructions, the
module must then be locked to prevent any additional trees from being created. The procedures to create trees and to
lock the card can be found below in Section 3 "Secure Operation" of this document.
All services of the module are provided via TrustedFlash commands. The TrustedFlash commands are passed to the
module using standard SD Write and Read commands. Therefore, from the host point of view, sending a
TrustedFlash command means writing data to a special file on the memory device used as the buffer file. Getting

